1.Evaluating a DBA Job Offer
Here are some useful questions to ask:
• Does the company offer regular training for its DBAs to learn new DBMS features and functionality? What about training for related technologies such as programming, networking, e-business, transaction management, message queuing, and the like?
• Does the company allow DBAs to regularly attend local user groups? 12 What about annual user groups at remote locations?
• Are there backup DBAs, or will you be the only one on call 24/7?
• Are there data administration and system administration organizations, or are the DBAs expected to perform all of these duties, too?
• Does the DBA group views its relationship with application development groups as a partnership? Or is the relationship more antagonistic?
• Are DBAs included in design reviews, budgeting discussions, and other high-level IT committees and functions?
2.DBA versus DA
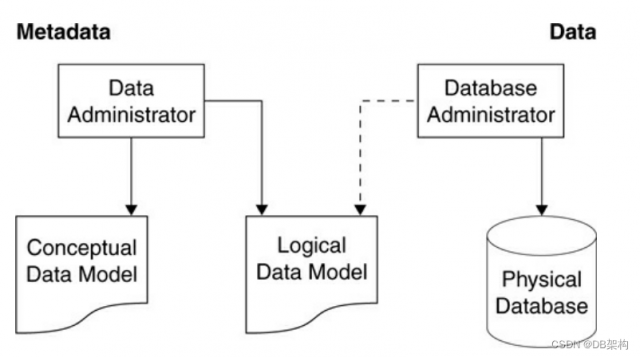
The DBA is the conduit for communication between the DA team and the technicians and application programming staff.
3.System Administration
When the SA role exists separately from the DBA role, it is responsible for the installation and setup of the DBMS. The system administrator (SA) typically has no responsibility for database design and supportthe DBA is responsible for the databases and the SA is responsible for DBMS installation, modification, and support
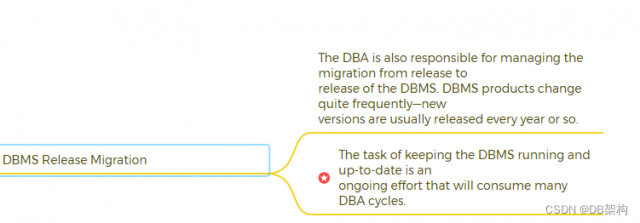
The system administrator ensures that the IT infrastructure is operational for database development by setting up the DBMS appropriately, applying ongoing maintenance from the DBMS vendor, and coordinating migration to new DBMS releases and versions.
The SA will never understand the physical database like a DBA, but the DBA is unlikely to understand the installation and in-depth technical relationships of system software like the SA.
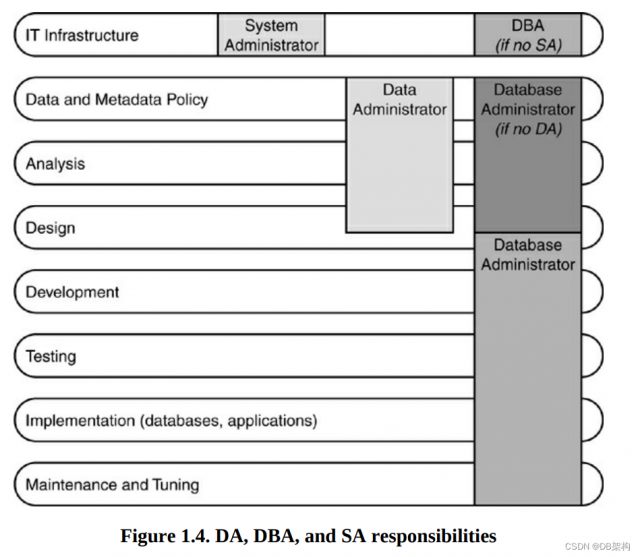
DA , DBA, and SA reponsibilities
4.DBA Tasks
A DBA must be capable of performing many tasks to ensure that the organization’s data and databases are useful, usable, available, and correct. These tasks include design, performance monitoring and tuning, ensuring availability, authorizing security, backup and recovery, ensuring data integrity, and, really, anything that interfaces with the company’s databases.
4.1 Database Design
The DBA must be able to transform a logical data model into a physical database.
The DBA must be able to transform a logical data model into a physical database implementation. The DBA must ensure that the database design and implementation will enable a useful database for the applications and clients that will use it.
A DBA will most likely spend more time administering and tuning databases than in originally designing and building databases.
A poor relational design can result in poor performance, a database that does not meet the needs of the organization, and potentially inaccurate data.
4.2 Performance Monitoring and Tuning
Five factors influence database performance: workload(负载), throughput(吞吐量), resources(资源), optimization(最优化), and contention(资源竞争).
4.2.1 Workload
The Workload that is requested of the DBMS defines the demand. It is a combination of online transactions , batch jobs, ad hoc queries, datawarehousing and analytical queries, and commands directed through the system at any given time.Workload can fluctuate drastically from day to day,hour to hour, minute to minutes, and even second to second.The overall workload has a major impact on database performance.
4.2.2 Throughput
Throughput define the overall capability of the computer hardware and software to process. It is a composite of I/O speed, CPU speed, parallel capabilities of the machine, and the efficienct of the operating system and system software. The hardware and software tools at the disposal of the system are known as the resources of the system. Examples include the database kernel, disk space, cache controllers, and microcode.
4.2.3 Optimization
All types of systems can be optimized, but relational queries are unique in that optimization is primarily accomplished internal to the DBMS. However, there are many other factors that need to be optimized (SQL formulation, database parameters, programming efficiently, and so on) to enable the database optimizer to create the most efficient access paths.
4.2.4 Contention
When the demand (workload) for a particular resource is high, contention can result.
Contention is the condition in which two or more components of the workload are attempting to use a single resource in a conflicting way (for example, dual updates to the same piece of data). As contention increases, throughput decreases.
Therefore,
database performance can be defined as the optimization of resource usage to increase throughput and minimize contention, enabling the largest possible workload to be processed.
Many performance management tasks must be shared between the DBA and other technicians. In other words, handling performance problems is truly an enterprise-wide endeavor.
Database performance can be defined as the optimization of resource usage to increase throughput and minimize contention, enabling the largest possible workload to be processed.
Alerts can be set up to e-mail the DBA when performance metrics are not within accepted boundaries.
Many tasks and abilities are required of DBAs to ensure efficient access to databases. Some of these abilities include
- building appropriate indexes
- specifying large enough buffers and caches
- aligning the database implementation with the IT infrastructure,
- ongoing monitoring of databases and applications
- database reorganization
- adapting to business changes —more users, more data, additional processing, and changing requirements and regulations.
4.3 Ensuring Availability
Availability of data and databases is often closely aligned with performance, but it is actually a separate concern. Of course, if the DBMS is offline, performance will be horrible because no data can be accessed. But ensuring database availability is a multifaceted process.
Ensuring database availability is a multi-faceted process.
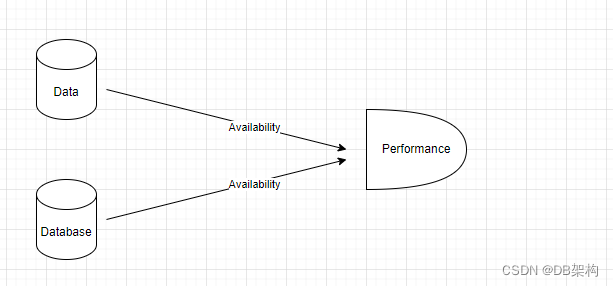
1.The data of availiablity is
- keeping the DBMS up and running.
- Vigilant monitoring and automated alerts can be used to warn of DBMS outages
- Call for corrective action.
2. The database of availiability is
- minimizing the amount of downtime required to perform administrative tasks.
The DBA must understand all of these aspects of availability and ensure that each application is receiving the correct level of availability for its needs
4.4 Database Security and Authorization
It is the responsibility of the DBA to ensure that data is available only to authorized users.
Grant and Revoke
Security must be administered for many actions required by the database environment:
• Creating database objects, including databases, tables, views, and program structures
• Altering the structure of database objects
• Accessing the system catalog
• Reading and modifying data in tables
• Creating and accessing user-defined functions and data types
• Running stored procedures
• Starting and stopping databases and associated database objects
• Setting and modifying DBMS parameters and specifications
• Running database utilities such as LOAD, RECOVER, and REORG
Database security can be enforced in other ways as well.
- views can be created to block sensitive columns or rows from being viewed by end users and programmers.
- DBA also frequently interfaces with external security methods when they impact database security.
- SQL injection attacks and how to prevent them need to be regarded.
The DBA must understand the aspects of security that impact access to databases.
4.5 Governance and Regulatory Compliance
Assuring compliance with industry and governmental regulations is an additional task required of database administration, at least in terms of implementing proper controls.s. The DBA must work with management, auditors, and business experts to understand the regulations that apply to their industry and the manner in which data is treated.
Certain aspects of regulatory compliance address standard DBA operating procedures.
regulations may contain
- language enforcing specific security
- authorization procedures
- auditing requirements
- data backup specifications
- change management procedures.
DBAs set the proper technological controls and procedures for compliance with regard to the treatment of data.
4.6 Backup and Recovery
The DBA must be prepared to recover data in the event of a problem.
“Problem” can mean anything from a system glitch or program error to a natural disaster that shuts down an organization.
The majority of recoveries today occur as a result of application software error and human error.
Hardware failures are not as prevalent as they used to be.
In fact, analyst estimates indicate that 80 percent of application errors are due to software failures and human error. The DBA must be prepared to recover data to a usable point, no matter what the cause, and to do so as quickly as possible.
The majority of recoveries today occur as a result of application software error and human error.
The first type of data recovery that usually comes to mind is a recover to current, usually in the face of a major shutdown.The end result of the recovery is that the database is brought back to its current state at the time of the failure. Applications are completely unavailable until the recovery is complete.
Another type of traditional recovery is a point-in-time recovery. Point-in-time recovery usually is performed to deal with an application-level problem. Conventional techniques to perform a point-in-time recovery will remove the effects of all transactions since a specified point in time. This sometimes can cause problems if there were some valid transactions during that time frame that still need to be applied.
Transaction recovery is a third type of recovery that addresses the shortcomings of the traditional types of recovery: downtime and loss of good data. Thus, transaction recovery is an application recovery whereby the effects of specific transactions during a specified time frame are removed from the database. Therefore, transaction recovery is sometimes referred to as application recovery.

4.7 Ensuring Data Integrity
A database must be designed to store the correct data in the correct way without that data becoming damaged or corrupted.

4.8 DBMS Release Migration
4.9 Jack-of-All-Trades
The IT infrastructure of today consists of things such as
• Programming languages and environments such as COBOL, Microsoft
Visual Studio, C/C++/C#, Java, and PHP
• Software frameworks such as .NET and J2EE
• Database and process design tools such as ERwin and Rational Rose
• Transaction processing systems such as CICS and Tuxedo
• Application servers such as WebSphere, JBoss, Oracle Application
Server, and EAServer
• Message queuing software such as MQSeries and MSMQ
• Networking software and protocols such as SNA, VTAM, and TCP/IP
• Networking hardware such as bridges, routers, hubs, and cabling
• Multiple operating systems such as Windows, z/OS and MVS, UNIX
and Linux, and perhaps others
• Data storage hardware and software such as enterprise storage servers,
Microsoft SMS, IBM DFHSM, SANs, and NAS
• Operating system security packages such as RACF, ACF2, and
Kerberos
• Other types of storage hardware, for example, tape machines, silos, and
solid-state (memory-based) storage
• Non-DBMS data set and file storage techniques such as VSAM and btree
• NoSQL products such as Hadoop and MongoDB
• Database administration tools and how they interface with other
systems management solutions
• Systems management tools and frameworks such as HP OpenView and
CA Unicenter
• Operational control software such as batch scheduling software and job
entry subsystems
• Software distribution solutions for implementing new versions of
system software across the network
• The Internet and Web-enabled databases and applications
• Client/server development techniques (multitier, fat server/thin client,
thin server/fat client, etc.)
• Object-oriented and component-based development technologies and
techniques such as CORBA, COM, OLE/DB, ADO, and EJB
• Pervasive computing technology devices such as tablets and
smartphones
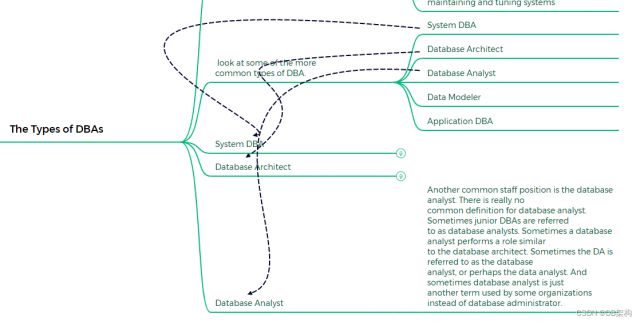
5.The Types of DBAs
5.1 System DBA

5.2 Database Architect

5.3 Database Analyst
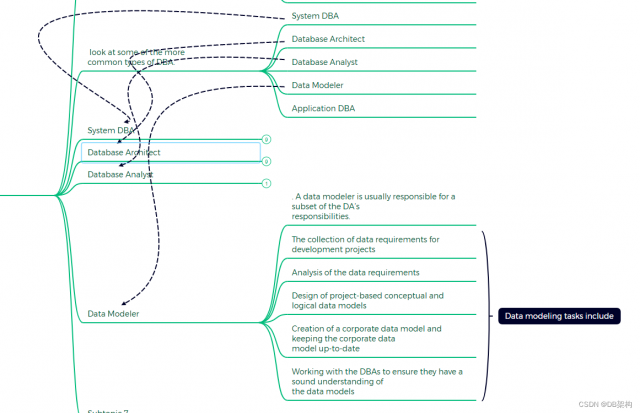
5.4 Data Modeler
5.5 Application DBA


5.6 Task-Oriented DBA
Larger organizations sometimes create very specialized DBAs who focus on a single specific DBA task.
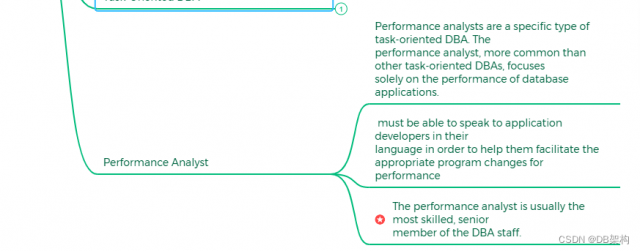
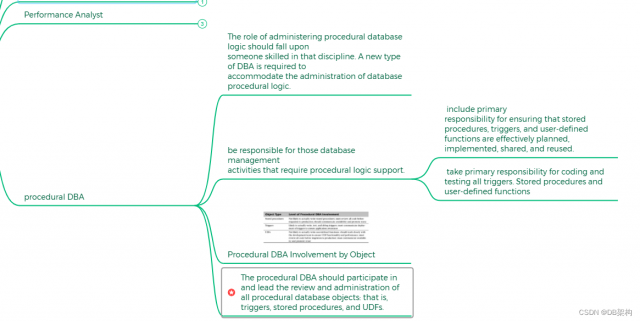
5.7 Performance Analyst
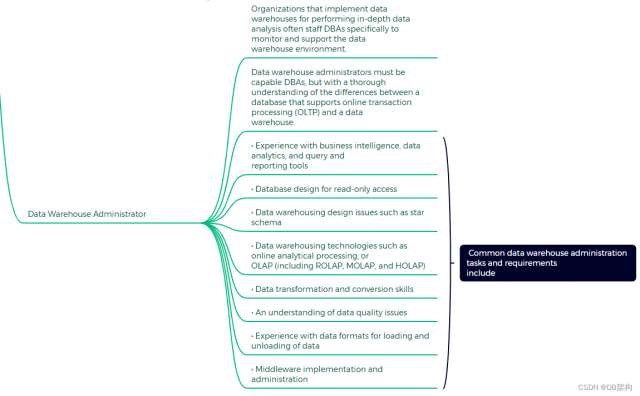
5.8 Data Warehouse Administrator
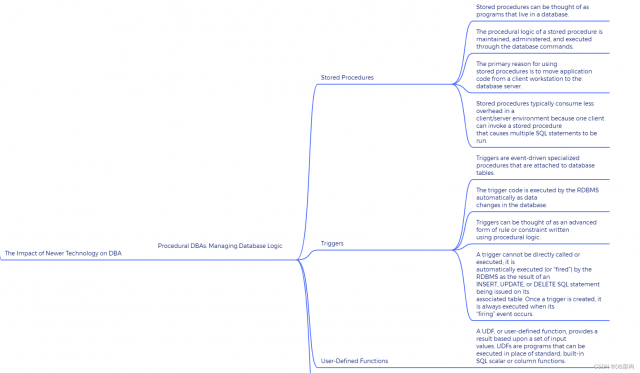
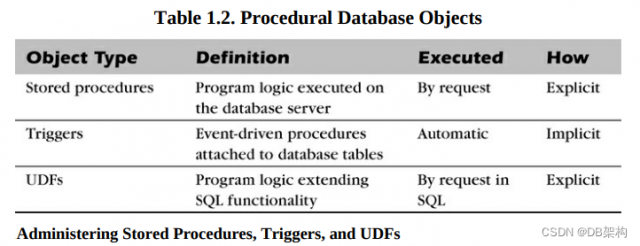
5.9 Procedual DBA
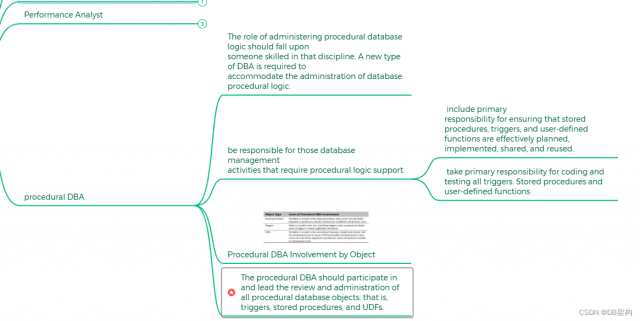
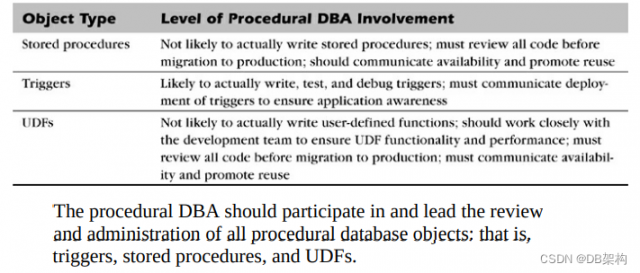
Procedural DBA Involvement by Object

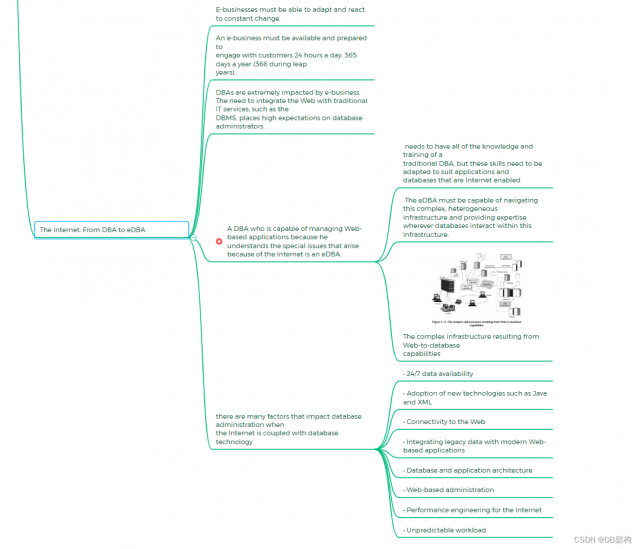
5.10 The Internet From DBA to eDBA

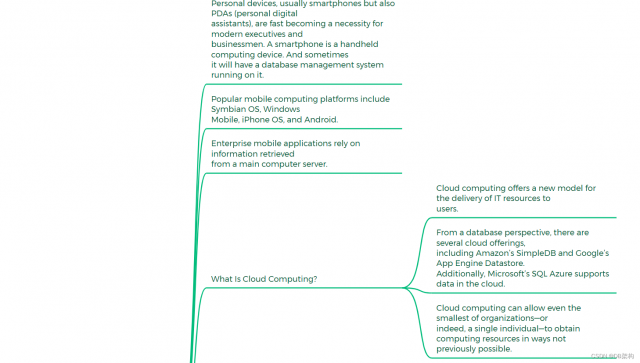
5.11 The Personal DBA and the Cloud



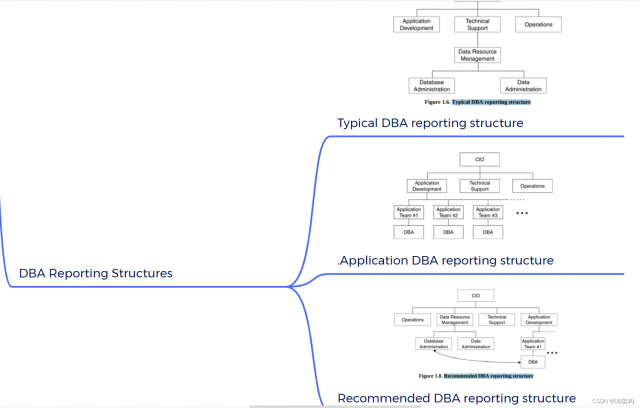
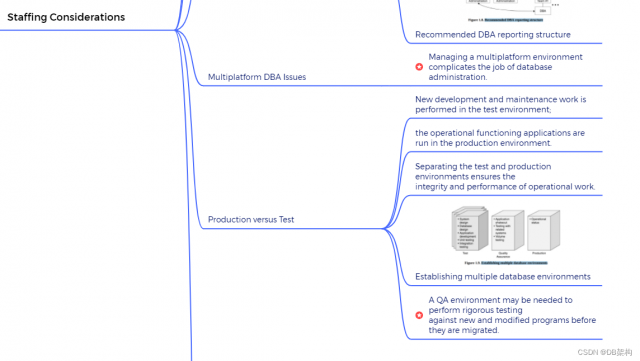
6. Staffing Considerations

Administering Stored Procedures, Triggers, and UDFs
本文链接:https://my.lmcjl.com/post/19254.html

4 评论